302 lines
4.6 KiB
Markdown
302 lines
4.6 KiB
Markdown
---
|
|
_class: lead
|
|
paginate: true
|
|
backgroundColor: #fff
|
|
---
|
|
|
|
<style>
|
|
/* Changed in Marp 4.0.0. Re-center. */
|
|
section.lead {
|
|
display: flex;
|
|
}
|
|
|
|
div.two-columns {
|
|
column-count: 2;
|
|
}
|
|
</style>
|
|
|
|
|
|

|
|
|
|
---
|
|
|
|
# Anton Livaja
|
|
|
|
Co-Founder & Security Engineer at Distrust (https://distrust.co)
|
|
|
|
* Firm specializing in high assurance security consulting and engineering.
|
|
|
|
* Clients: blockchain labs and companies, fin-tech, hedge funds, exchanges,
|
|
electrical grid operators, healthcare providers, etc.
|
|
|
|
---
|
|
|
|
# Trends in Supply Chain Security
|
|
|
|
"[Supply chain threats increased by 1300% between 2020 and 2023]"
|
|
|
|
- 2025 Software Supply Chain Security Report by ReversingLabs.
|
|
|
|
---
|
|
|
|
# Linux Usage Statistics
|
|
|
|
* 70%+ servers run Linux
|
|
|
|
* ~5% desktop / laptop users use Linux
|
|
|
|
* ~12 widely used Linux distributions
|
|
|
|
---
|
|
|
|
# Open Source vs Proprietary
|
|
|
|
* High risk environments require verifiability
|
|
|
|
* Proprietary software = security through obscurity
|
|
|
|
---
|
|
|
|
# What is a "Linux Distribution"
|
|
|
|
* Linux kernel
|
|
|
|
* Software "packages"
|
|
|
|
* Package manager
|
|
|
|
* But they are not all equal...
|
|
|
|
---
|
|
|
|
# Linux Distribution Security
|
|
|
|
* What machine are packages built on?
|
|
|
|
* Who maintains your Linux packages?
|
|
|
|
* How are the packages delivered?
|
|
|
|
---
|
|
|
|
# Anatomy of a Package
|
|
|
|
* Mainainer creates a "package"
|
|
|
|
* The package is reviewed
|
|
|
|
* A centralized server builds the binary and signs it
|
|
|
|
---
|
|
|
|
# Underutilized Strategies
|
|
|
|
* Reproducible / deterministic builds
|
|
|
|
* Full source bootstrapping
|
|
|
|
* Cryptographic signing
|
|
|
|
---
|
|
|
|
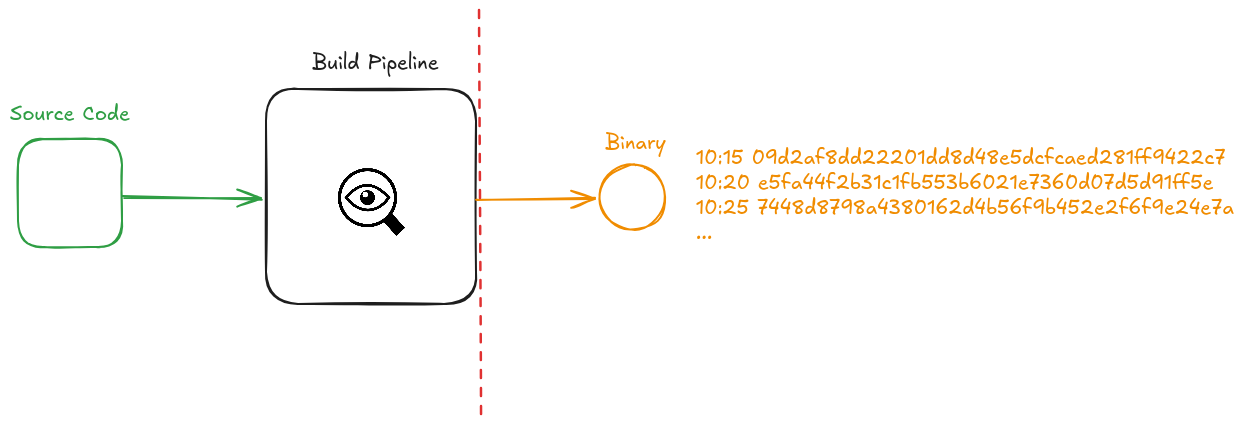
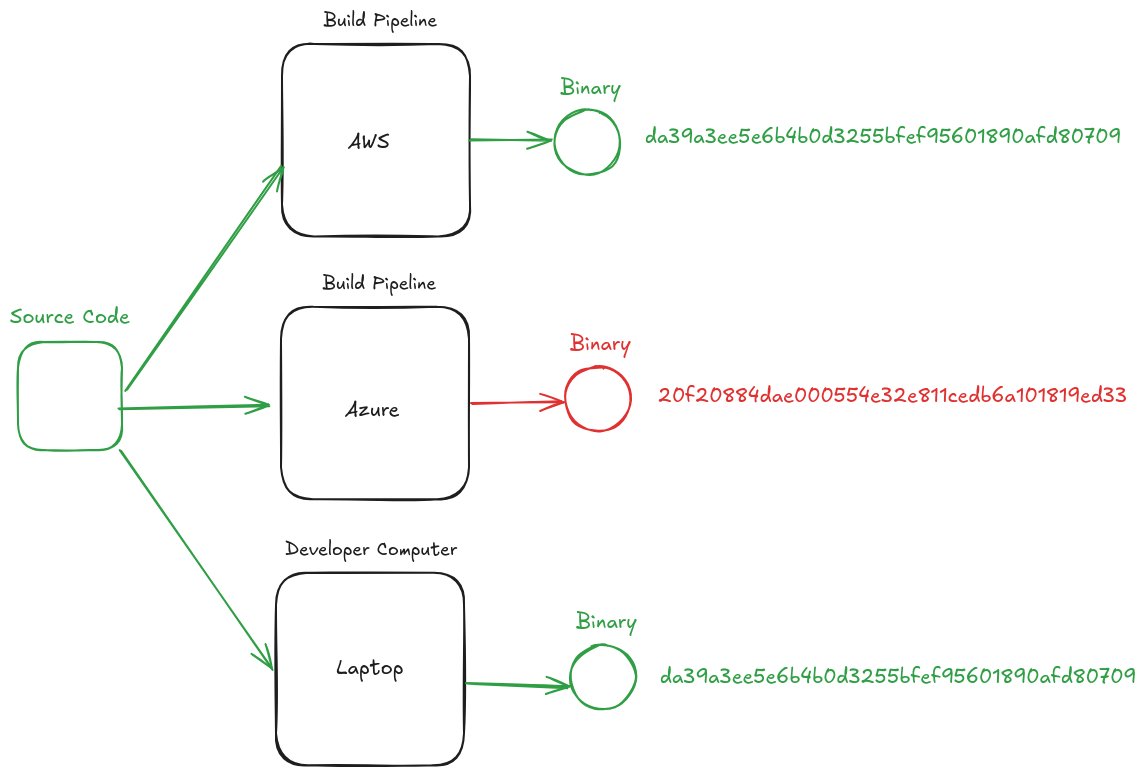
# Reproducibility / Determinism
|
|
|
|
---
|
|
|
|

|
|
|
|
---
|
|
|
|
|
|
|
|
---
|
|
|
|
|
|
|
|
---
|
|
|
|
# How Deep Do We Have to Go?
|
|
|
|
* Compiler
|
|
|
|
* Build and Runtime Environment
|
|
|
|
* Operating System + Packages
|
|
|
|
* Additional CLI / Tools
|
|
|
|
* Software Application
|
|
|
|
* First Party Code
|
|
|
|
* Third Party Code
|
|
|
|
---
|
|
|
|
# Full Source Bootstrapping
|
|
|
|
---
|
|
|
|

|
|
|
|
---
|
|
|
|
# Who Compiles the Compiler?
|
|
|
|
* Mostly downloaded as a binary
|
|
|
|
* Even if the compiler is built from source, usually another compiler is used to do so
|
|
|
|
* This means there is no clear providence to how we went from nothing to having a usable compiler
|
|
|
|
---
|
|
|
|
# Bootstrapping Compilers
|
|
|
|
* Consists of "stages", and hundreds of steps of starting from a human auditable rudimentary compiler and building up all the way up to a modern compiler
|
|
|
|
* Bootstrapping programming languages
|
|
|
|
---
|
|
|
|
# Cryptographic Signing
|
|
|
|
* Code signing
|
|
|
|
* Artifact signing
|
|
|
|
* Multi-person signing
|
|
|
|
---
|
|
|
|

|
|
|
|
|
|
---
|
|
|
|
# [Stageˣ]
|
|
|
|
Open source Linux Distribution
|
|
|
|
* Minimal, bootstrapped, hermetic, and deterministic
|
|
|
|
---
|
|
|
|

|
|
|
|
---
|
|
|
|

|
|
|
|
---
|
|
# Full source bootstrapped from Stage 0
|
|
|
|
From a <190 byte compiler written in machine code, StageX bootstraps all the
|
|
compiler tools necessary to build the distribution, 100% deterministically.
|
|
|
|
- Stage 0: Getting a basic C compiler on x86 from hex0
|
|
- Stage 1: Building GCC for x86
|
|
- Stage 2: Upgrading GCC for x86_64
|
|
- Stage 3: Building up-to-date toolchains
|
|
- Stage X: Shipping the software you know and love
|
|
|
|
---
|
|
|
|
# A Rust Example
|
|
|
|
```dockerfile
|
|
FROM stagex/pallet-rust@sha256:b5bb9d8014a0f9b1d61e21e796d78dccdf1352f23cd32812f4850b878ae4944c AS build
|
|
ADD . /src
|
|
WORKDIR /src
|
|
ARG TARGET x86_64-unknown-linux-musl
|
|
RUN cargo build --release --target ${TARGET}
|
|
|
|
FROM scratch
|
|
COPY --from=build /app/target/${TARGET}/release/hello /usr/bin/hello
|
|
CMD ["/usr/bin/hello"]
|
|
```
|
|
|
|
---
|
|
|
|
# All packages in StageX are:
|
|
|
|
* Built using hash-locked sources
|
|
|
|
* Confirmed reproducible by multiple developers
|
|
|
|
* Signed by multiple release maintainers
|
|
|
|
---
|
|
|
|
# Pallets
|
|
|
|
StageX offers prebuilt containers including all the packages necessary to run some of our most used software, such as:
|
|
|
|
- `rust`
|
|
- `go`
|
|
- `nodejs`
|
|
- `nginx`
|
|
- `redis`
|
|
- `postgres`
|
|
|
|
---
|
|
|
|

|
|
|
|
---
|
|
|
|
# QubesOS
|
|
|
|
---
|
|
|
|
# Key Takeaways
|
|
|
|
* Full-source bootstrap
|
|
|
|
* Use bit for bit determinism
|
|
|
|
* Leverage cryptographic signing
|
|
|
|
---
|
|
|
|
# What's Next?
|
|
|
|
* Adding SBOM
|
|
|
|
* Packaging more software
|
|
|
|
* Fully automating software updates
|
|
|
|
* Additional container runtimes like Podman and Kaniko
|
|
|
|
* Additional chip architecture support such as ARM and RISC-V
|
|
|
|
---
|
|
|
|
# How You Can Help
|
|
|
|
* Provide feedback
|
|
|
|
* Support with development efforts
|
|
|
|
* Become a sponsor
|
|
|
|
---
|
|
|
|
# Links
|
|
|
|
**Email**: anton@distrust.co / sales@distrust.co
|
|
|
|
**Matrix Chat**: #stagex:matrix.org
|
|
|
|
**Docker Hub**: https://hub.docker.com/u/stagex
|
|
|
|
**Git Repo**: https://codeberg.org/stagex/stagex
|
|
|
|
**AirgapOS**: https://git.distrust.co/public/airgap
|
|
|
|
**EnclaveOS**: https://git.distrust.co/public/enclaveos
|
|
|
|
|
|
|