16 KiB
| _class | paginate | backgroundColor |
|---|---|---|
| lead | true |
Expanding (Dis)Trust
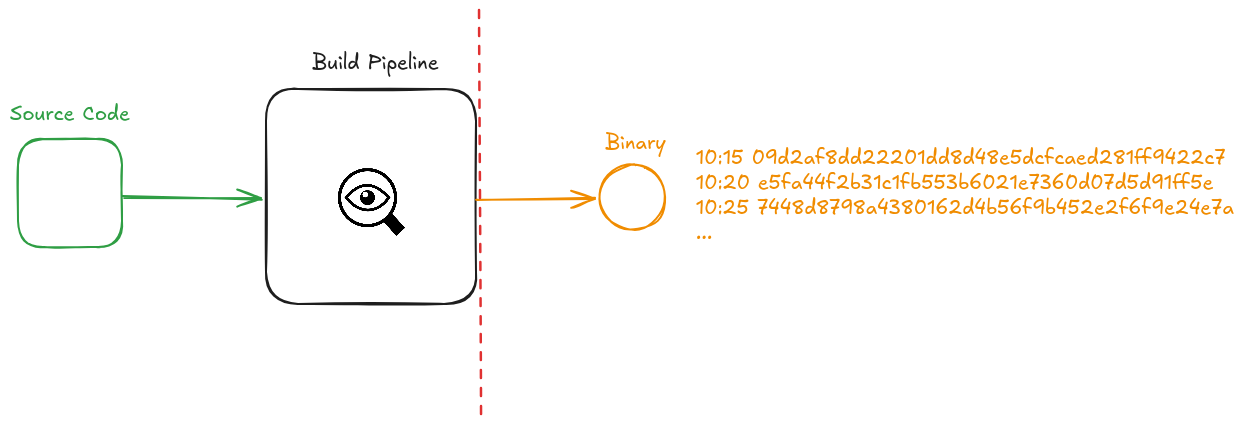
How can we prove that our software has not been tampered during build time?
- Binary - software that's in a format computers can work with
- Compiler - builds software into binaries
- Hashing - takes a data set and produces a fixed length string
- 8a1aaf746ada2a80fab03a58c91575ffe82885ac "banana"
- 9144b7b25e83a315de79e7a527f5631f9d4dacf2 "banan"
Anton Livaja
Co-Founder & Security Engineer at Distrust (https://distrust.co)
-
Firm specializing in high assurance security consulting and engineering.
-
Mission: to improve the security, privacy and freedom of as many people as possible through working on fundamental security problems and creating open source solutions.
-
Clients: electrical grid operators, healthcare providers, fin-tech companies and more.
Ken Thompson's Reflections on Trusting Trust
[The moral is obvious. You can't trust code that you did not totally create yourself. (Especially code from companies that employ people like me.) No amount of source-level verification or scrutiny will protect you from using untrusted code...]
What's the Answer?
-
Integrity hashes are already widely used
- How do we use them to verify the integrity of software during build time, not after?
-
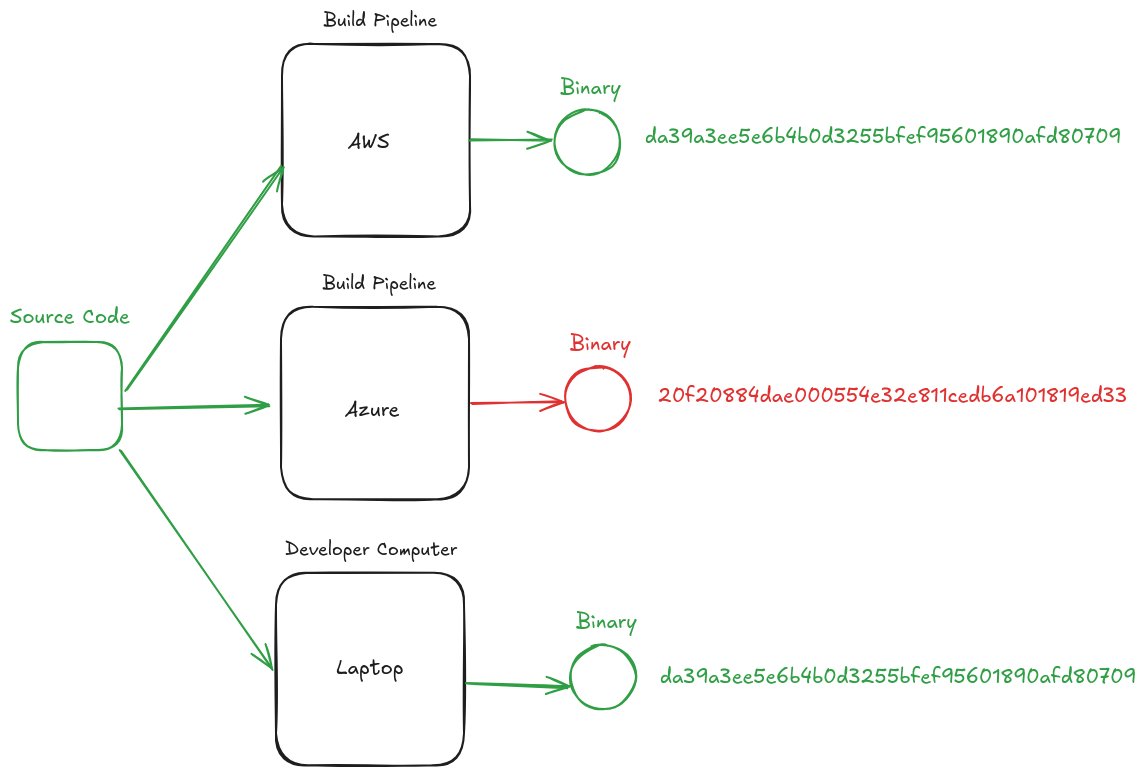
Determinism / Reproducibility
-
Method of building software which ensures that the resulting binary for a piece of software is always bit-for-bit identical.
-
-
When something is bit-for-bit identical each time it is deterministic
-
Once something is deterministic, it can be reproduced
How Deep Do We Have to Go?
-
Software Application
- First Party Code
- Third Party Code
-
Build and Runtime Environment
- Operating System + Packages
- Additional CLI / Tools
-
Compiler
Adequate Solution
-
Allows us to make the whole tree deterministic
-
Can be easily reproduced
-
Drop in replacement / easy to upgrade
Bootstrapping our Way Up
Who Compiles the Compiler?
-
Mostly downloaded as a binary
-
Even if the compiler is built from source, usually another compiler is used to do so
-
This means there is no clear providence to how we went from nothing to having a usable compiler
Bootstrapping Compilers
-
Consists of "stages", and hundreds of steps of starting from a human auditable rudimentary compiler and building up all the way up to a modern compiler
-
Bootstrapping programming languages
We Have a Compiler, Now What?
- Build all of the different dependencies we need:
linux kernelbashopensslgit- Yes... I mean everything in your build environment
Status Check-In
- So far we have established we need the following for a solution:
- Bootstrap a compiler in a deterministic manner
- Use compiler to build all our dependencies
- Last thing remaining: your application
[Stageˣ]
Open source Linux Distribution
Multi-Signed, Bootstrapped, Deterministic, and Minimal
| Distribution | Signatures | Libc | Bootstrapped | Reproducible | Rust deps |
|---|---|---|---|---|---|
| Stagex | 2+ Human | Musl | Yes | Yes | 4 |
| Debian | 1 Human | Glibc | No | Partial | 231 |
| Arch | 1 Human | Glibc | No | Partial | 127 |
| Fedora | 1 Bot | Glibc | No | No | 167 |
| Alpine | None | Musl | No | No | 41 |
Full source bootstrapped from Stage 0
From a 256-byte compiler written in hex0, StageX bootstraps all the compiler tools necessary to build the distribution, 100% deterministically.
- Stage 0: Getting a basic C compiler on x86
- Stage 1: Building GCC for x86
- Stage 2: Upgrading GCC for x86_64
- Stage 3: Building up-to-date toolchains
- Stage X: Shipping the software you know and love
A Rust Example
FROM stagex/pallet-rust@sha256:b5bb9d8014a0f9b1d61e21e796d78dccdf1352f23cd32812f4850b878ae4944c AS build
ADD . /src
WORKDIR /src
ARG TARGET x86_64-unknown-linux-musl
RUN cargo build --release --target ${TARGET}
FROM scratch
COPY --from=build /app/target/${TARGET}/release/hello /usr/bin/hello
CMD ["/usr/bin/hello"]
All packages in StageX are:
- Built using hash-locked sources
- Confirmed reproducible by multiple developers
- Signed by multiple release maintainers
Multi-Signed OCI Images
Pallets
StageX will soon offer prebuilt containers including all the packages necessary to run some of our most used software, such as:
rustgonodejsnginxredispostgres
Key Takeaways
- Bootstrapped compiler
- Fully deterministic
- Packages the software you're already using, but in a more secure manner.
- Is a drop in replacement, and has native container support
What's Next?
-
Adding SBOM
-
Packaging more software
-
Fully automating software updates
-
Additional container runtimes like Podman and Kaniko
-
Additional chip architecture support such as ARM and RISC-V
How You Can Help
-
Provide feedback
-
Support with development efforts
-
Become a sponsor
Links
Email: anton@distrust.co / sales@distrust.co
Matrix Chat: #stagex:matrix.org
Docker Hub: https://hub.docker.com/u/stagex
Git Repo: https://codeberg.org/stagex/stagex
Big thank you to sponsors who have supported the development of this project:
Turnkey, Distrust, Mysten Labs
Thank you to InCyber for hosting this fantastic event!